reduce scope of GitHub permissions required #22
Labels
No Label
Copied from Github
Kind/Breaking
Kind/Bug
Kind/Documentation
Kind/Enhancement
Kind/Feature
Kind/Security
Kind/Testing
Priority
Critical
Priority
High
Priority
Low
Priority
Medium
Reviewed
Confirmed
Reviewed
Duplicate
Reviewed
Invalid
Reviewed
Won't Fix
Status
Abandoned
Status
Blocked
Status
Need More Info
No Milestone
No project
No Assignees
2 Participants
Notifications
Due Date
No due date set.
Dependencies
No dependencies set.
Reference: cerc-io/snowballtools-base#22
Loading…
Reference in New Issue
Block a user
No description provided.
Delete Branch "%!s()"
Deleting a branch is permanent. Although the deleted branch may continue to exist for a short time before it actually gets removed, it CANNOT be undone in most cases. Continue?
the GitHub client should only request read permissions from public / private repos
the GitHub client also shows private repos of the org being used for the app
Scope of GitHub permissions has been set to
public_repoanduserhttps://docs.github.com/en/apps/oauth-apps/building-oauth-apps/scopes-for-oauth-apps#available-scopes
userscope is required to list orgs user is a part of and create repos in selected orgThe
stagingbranch has been rebased ontomainand now includes the above changeApp has been redeployed https://deploy.apps.vaasl.io
NOTE: The oauth app (
Deploy Appowned bylaconic-templates) needs to be revoked to see changes in permissions on connecting GitHub againhttps://github.com/settings/applications
confirming private repos don't show up anymore, however,
This application will be able to read and write all public repository data. The app shouldn't have to to require perms to write to repos.Write perms to create a new repo is 👍
Write perms to write to existing/new repo is 👎
According to the available GitHub OAuth scopes, there is no scope that allows for creating a new repository without also granting write access to existing or newly created repositories
https://docs.github.com/en/apps/oauth-apps/building-oauth-apps/scopes-for-oauth-apps#available-scopes
Currently, the
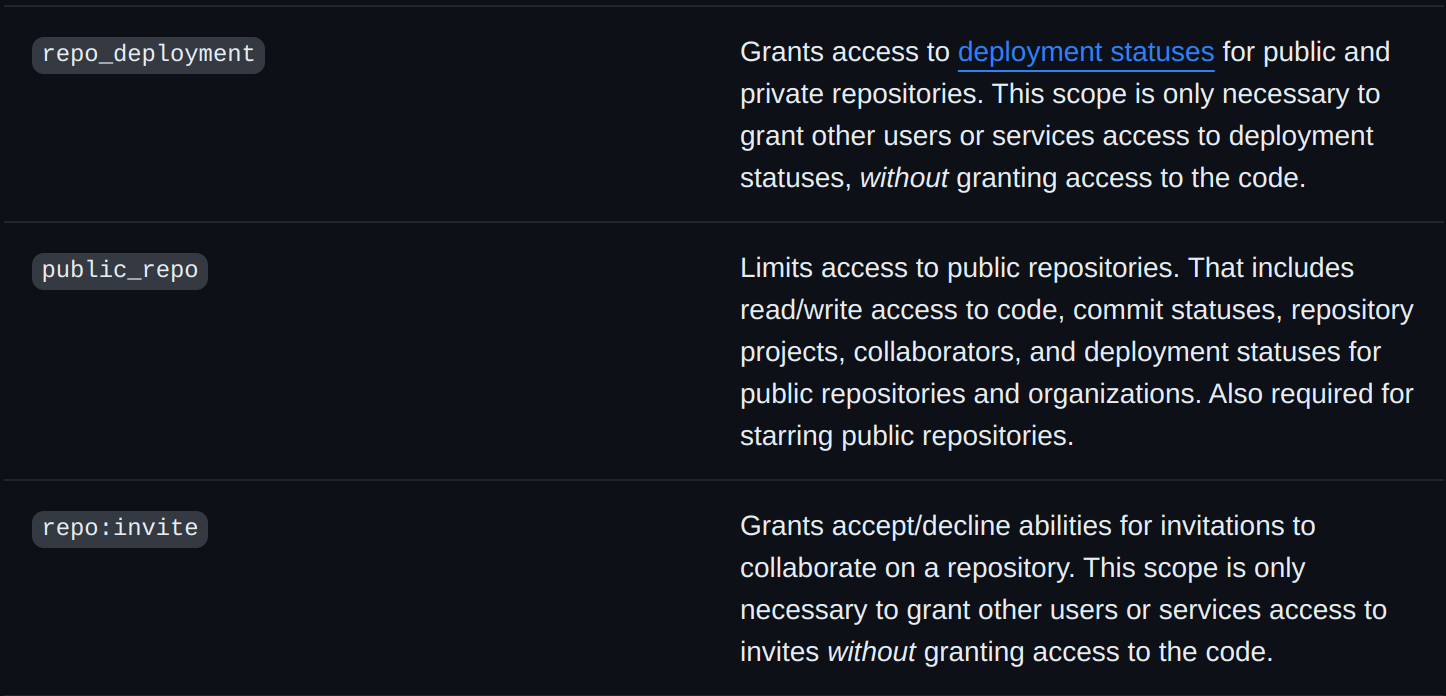
public_reposcope is used, which includes read/write access to code, commit statuses, repository projects, collaborators, and deployment statuses for public repositories and organizationsoof. here's to hoping gitea has finer grained perms...